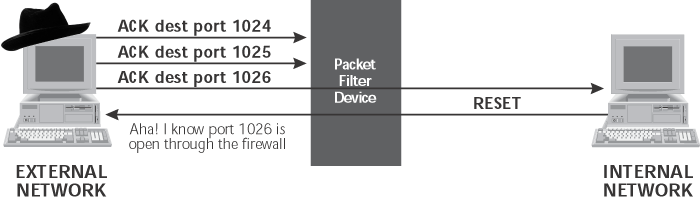
Figure 6.9 ACK
scanning
¨TCP ACK (-sA)
–Allows attacker to determine what kind of established
connections a firewall or router will allow into a network by determining which ports through a firewall allow
established connection responses
–If no response or an ICMP Port Unreachable message is
returned, Nmap will label the target port as “filtered”, meaning that a packet filter is blocking the
response